What is a firewall?
A firewall is a software program or piece of hardware (like, Network Router) that helps screen out hackers, viruses, and worms that try to reach your computer over the Internet, But How firewall can keep you away from Hackers or unwanted viruses,
It does this by capturing/filtering network traffic of this Computer, Categories traffic as Inbound traffic or OutBound traffic, Use pre-Defined Rules/Filters, and perform action such as, Allow/Block traffic.
Types of Firewall Rules
There can be only two types of Traffic, inbound traffic or outbound traffic, Therefore, There are two Rules for Windows Firewall.
-
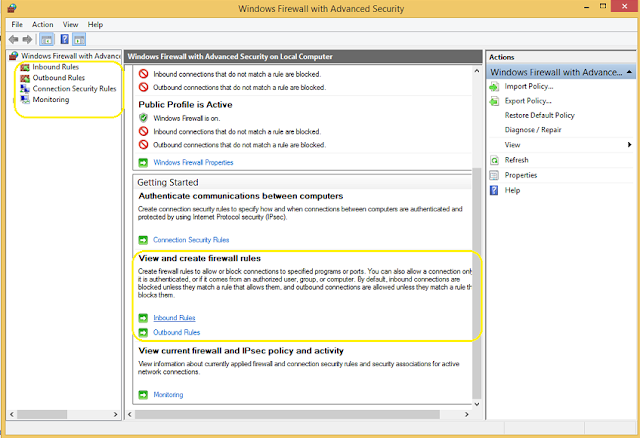
Inbound Rule (Let Program receive traffic from *Other_Sources)

-
Outbound Rule (Let Program send traffic to *Other_Sources)
*Other_Sources such as, Programs, system services, computers, or users
- Custom Windows Firewall Rules serve three purposes
- Allow the connection
- Allow a connection only if it is secured through the use of Internet Protocol security (IPsec)
- Block the connection
Windows Firewall
Default Behavior for Inbound/Outbound traffic
- Inbound traffic is blocked by Default on Windows, So If you wanna use any Application/Software, Which will share something over your Network, Windows Firewall will prompt you to create/allow Inbound Connection.
- Outbound traffic is allowed by default, But (Generally) You wanna create Outbound Rule, to Block Connection for Any Application/Software.
Why Windows Firewall has Domain, Private and Public Profiles?
Windows Firewall can automatically detect, which type of network you wanna connect to, So it will prompt you to Choose Proper Network Profile for that Network Connection, For Example, If You want to connect to your
Home Router, Dongle etc, Windows will Recommend You to Choose, Private network Profile for this Network Connection. And When You want to connect to Public Network such as Public Wifi, LAN etc, Windows will detect it as Public Network as Recommend you to Choose Public Network Profile, Basically Public Network Profile is Configured as Most Secure than other two network profiles.Note: Windows Firewall has advanced settings for these profiles.
How to Check/Configure your Current/Active Network Profile
You can check/configure current/active network profile in
Windows Network and Sharing CenterHow to Disable Internet/OutBound Traffic for All Apps/Software
How to Create and Allow/Block Internet Traffic for Specific Application
- Create New Outbound Rule

- Browse for Application, to Filter its Traffic

- What you want to do, for Captured Traffic
- For Which Profile, You want to activate this Rule

- Unique Name and Optional Description for this NEW OutBound Rule

- Lets Verify Our Firewall Rule Properties

Create New InBound Rule
netsh advfirewall firewall add rule name="wget-me" profile=domain,private,public protocol=any enable=yes DIR=In program="%ProgramFiles%\Gnu-wget\wget.exe" Action=Allow
Create New OutBound Rule
netsh advfirewall firewall add rule name="wget-me" profile=domain,private,public protocol=any enable=yes DIR=Out program="%ProgramFiles%\Gnu-wget\wget.exe" Action=Allow
Change in Registry (Because of Command Above)
HKLM\SYSTEM\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy\FirewallRules\{994CCCA0-9C02-44DD-AB5F-02E74AD3E935}: "v2.20|Action=Allow|Active=TRUE|Dir=Out|App=%ProgramFiles%\Gnu-wget\wget.exe|Name=wget-me|"
HKLM\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\FirewallRules\{994CCCA0-9C02-44DD-AB5F-02E74AD3E935}: "v2.20|Action=Allow|Active=TRUE|Dir=Out|App=%ProgramFiles%\Gnu-wget\wget.exe|Name=wget-me|"
Remove Existing Rule
netsh advfirewall firewall delete rule profile=domain,private,public name="wget-me"
@C:\Windows\system32
=> netsh advfirewall /?
The following commands are available:
Commands in this context:
? - Displays a list of commands.
consec - Changes to the `netsh advfirewall consec' context.
dump - Displays a configuration script.
export - Exports the current policy to a file.
firewall - Changes to the `netsh advfirewall firewall' context.
help - Displays a list of commands.
import - Imports a policy file into the current policy store.
mainmode - Changes to the `netsh advfirewall mainmode' context.
monitor - Changes to the `netsh advfirewall monitor' context.
reset - Resets the policy to the default out-of-box policy.
set - Sets the per-profile or global settings.
show - Displays profile or global properties.
The following sub-contexts are available:
consec firewall mainmode monitor
To view help for a command, type the command, followed by a space, and then
type ?.
@C:\Windows\system32
=> netsh advfirewall firewall /?
The following commands are available:
Commands in this context:
? - Displays a list of commands.
add - Adds a new inbound or outbound firewall rule.
delete - Deletes all matching firewall rules.
dump - Displays a configuration script.
help - Displays a list of commands.
set - Sets new values for properties of a existing rule.
show - Displays a specified firewall rule.
To view help for a command, type the command, followed by a space, and then
type ?.
@C:\Windows\system32
=> netsh advfirewall firewall add rule /?
Usage: add rule name=<string>
dir=in|out
action=allow|block|bypass
[program=<program path>]
[service=<service short name>|any]
[description=<string>]
[enable=yes|no (default=yes)]
[profile=public|private|domain|any[,...]]
[localip=any|<IPv4 address>|<IPv6 address>|<subnet>|<range>|<list>]
[remoteip=any|localsubnet|dns|dhcp|wins|defaultgateway|
<IPv4 address>|<IPv6 address>|<subnet>|<range>|<list>]
[localport=0-65535|<port range>[,...]|RPC|RPC-EPMap|IPHTTPS|any (default=any)]
[remoteport=0-65535|<port range>[,...]|any (default=any)]
[protocol=0-255|icmpv4|icmpv6|icmpv4:type,code|icmpv6:type,code|
tcp|udp|any (default=any)]
[interfacetype=wireless|lan|ras|any]
[rmtcomputergrp=<SDDL string>]
[rmtusrgrp=<SDDL string>]
[edge=yes|deferapp|deferuser|no (default=no)]
[security=authenticate|authenc|authdynenc|authnoencap|notrequired
(default=notrequired)]
Remarks:
- Add a new inbound or outbound rule to the firewall policy.
- Rule name should be unique and cannot be "all".
- If a remote computer or user group is specified, security must be
authenticate, authenc, authdynenc, or authnoencap.
- Setting security to authdynenc allows systems to dynamically
negotiate the use of encryption for traffic that matches
a given Windows Firewall rule. Encryption is negotiated based on
existing connection security rule properties. This option
enables the ability of a machine to accept the first TCP
or UDP packet of an inbound IPsec connection as long as
it is secured, but not encrypted, using IPsec.
Once the first packet is processed, the server will
re-negotiate the connection and upgrade it so that
all subsequent communications are fully encrypted.
- If action=bypass, the remote computer group must be specified when dir=in.
- If service=any, the rule applies only to services.
- ICMP type or code can be "any".
- Edge can only be specified for inbound rules.
- AuthEnc and authnoencap cannot be used together.
- Authdynenc is valid only when dir=in.
- When authnoencap is set, the security=authenticate option becomes an
optional parameter.
Examples:
Add an inbound rule with no encapsulation security for browser.exe:
netsh advfirewall firewall add rule name="allow browser"
dir=in program="c:\programfiles\browser\browser.exe"
security=authnoencap action=allow
Add an outbound rule for port 80:
netsh advfirewall firewall add rule name="allow80"
protocol=TCP dir=out localport=80 action=block
Add an inbound rule requiring security and encryption
for TCP port 80 traffic:
netsh advfirewall firewall add rule
name="Require Encryption for Inbound TCP/80"
protocol=TCP dir=in localport=80 security=authdynenc
action=allow
Add an inbound rule for browser.exe and require security
netsh advfirewall firewall add rule name="allow browser"
dir=in program="c:\program files\browser\browser.exe"
security=authenticate action=allow
Add an authenticated firewall bypass rule for group
acmedomain\scanners identified by a SDDL string:
netsh advfirewall firewall add rule name="allow scanners"
dir=in rmtcomputergrp=<SDDL string> action=bypass
security=authenticate
Add an outbound allow rule for local ports 5000-5010 for udp-
Add rule name="Allow port range" dir=out protocol=udp localport=5000-5010 action=allow
@C:\Windows\system32
=> netsh advfirewall firewall delete rule /?
Usage: delete rule name=<string>
[dir=in|out]
[profile=public|private|domain|any[,...]]
[program=<program path>]
[service=<service short name>|any]
[localip=any|<IPv4 address>|<IPv6 address>|<subnet>|<range>|<list>]
[remoteip=any|localsubnet|dns|dhcp|wins|defaultgateway|
<IPv4 address>|<IPv6 address>|<subnet>|<range>|<list>]
[localport=0-65535|<port range>[,...]|RPC|RPC-EPMap|any]
[remoteport=0-65535|<port range>[,...]|any]
[protocol=0-255|icmpv4|icmpv6|icmpv4:type,code|icmpv6:type,code|
tcp|udp|any]
Remarks:
- Deletes a rule identified by name and optionally by endpoints, ports,
protocol, and type.
- If multiple matches are found, all matching rules are deleted.
- If name=all is specified all rules are deleted from the specified
type and profile.
Examples:
Delete all rules for local port 80:
netsh advfirewall firewall delete rule name=all protocol=tcp localport=80
Delete a rule called "allow80":
netsh advfirewall firewall delete rule name="allow80"
Query Information about pre-defined Rules
@rem -- Display All OutBound Firewall Rules
@C:\Users\ssp\Desktop
=> netsh advfirewall firewall show rule name=all dir=out
Rule Name: wget-me
----------------------------------------------------------------------
Enabled: Yes
Direction: Out
Profiles: Domain,Private,Public
Grouping:
LocalIP: Any
RemoteIP: Any
Protocol: Any
Edge traversal: No
Action: Allow
Rule Name: @{Microsoft.ZuneVideo_2.6.446.0_x64__8wekyb3d8bbwe?ms-resource://Microsoft.ZuneVideo/resources/IDS_MANIFEST_VIDEO_APP_NAME}
----------------------------------------------------------------------
Enabled: Yes
Direction: Out
Profiles: Domain,Private,Public
Grouping: Video
LocalIP: Any
RemoteIP: Any
Protocol: Any
Edge traversal: No
Action: Allow
.
.
.
Rule Name: Windows Media Player x86 (UDP-Out)
----------------------------------------------------------------------
Enabled: No
Direction: Out
Profiles: Domain,Private,Public
Grouping: Windows Media Player
LocalIP: Any
RemoteIP: Any
Protocol: UDP
LocalPort: Any
RemotePort: Any
Edge traversal: No
Action: Allow
Ok.




No comments :
Post a Comment